What’s up, everyone!
IT admins have the ability to manage certain applications with Microsoft Intune Mobile Application Management (MAM) from managed and unmanaged Android and iOS/iPadOS devices. The really cool thing is that admins now have the ability to secure connections to Windows 365 and Azure Virtual Desktop as well. In this post I will show you how to configure Intune MAM for Windows 365.
A short intro on Intune MAM
Imagine being able to enforce settings on an application basis instead of devices. An huge advantage would be that these settings can be enforced from unmanaged devices as well.
Let’s shift this idea to Windows 365. What if IT admins could restrict device redirections using Intune MAM? For example, allow local drive redirection for an unmanaged Android device or even include a check if the Android version is 13 or higher. Pretty powerful stuff, right?
As per Microsoft, admins currently can use Intune MAM on unmanaged devices to;
- Disable specific redirections on personal devices.
- Require PIN access to app before connection.
- Specify a minimum device operating system version before the connection.
- Specify a minimum Windows Ap and/or Remote Desktop app version number before connection.
- Block jailbroken/rooted devices from connecting.
- Require a mobile threat defense solution on devices, with no threats detected before connecting.
In this post I will use the Remote Desktop (android) app to block local drive redirection for unmanaged Android devices. Let’s find out how it works!
Configuring Intune MAM in Microsoft Intune
Configuring Intune MAM involves the following steps:
- Create an Intune device filter: differentiate between managed and unmanaged devices.
- Create an Intune app configuration policy: configure redirection settings. This will not require a conditional access policy.
- Create an Intune app protection policy: add device requirements that must be met. Mind you; this will require a Conditional Access policy!
- Create a conditional access policy: add the app configuration profile, and app protection profile if applicable, to control access to Windows 365 and/or Azure Virtual Desktop.
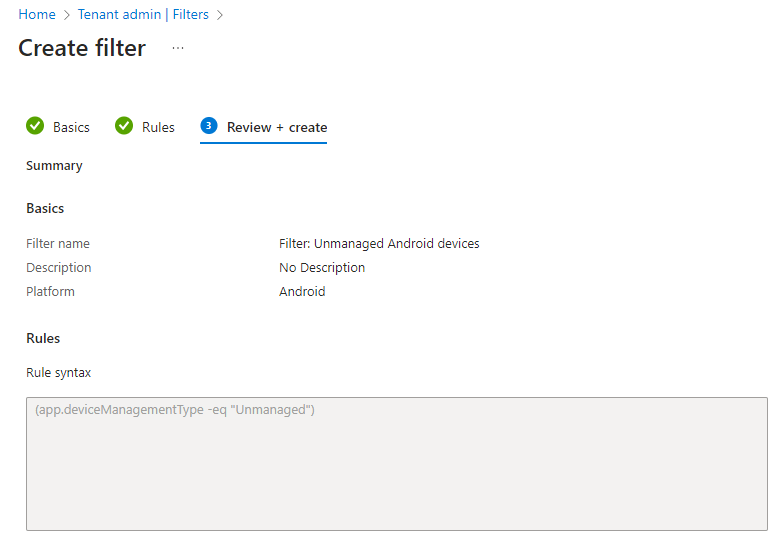
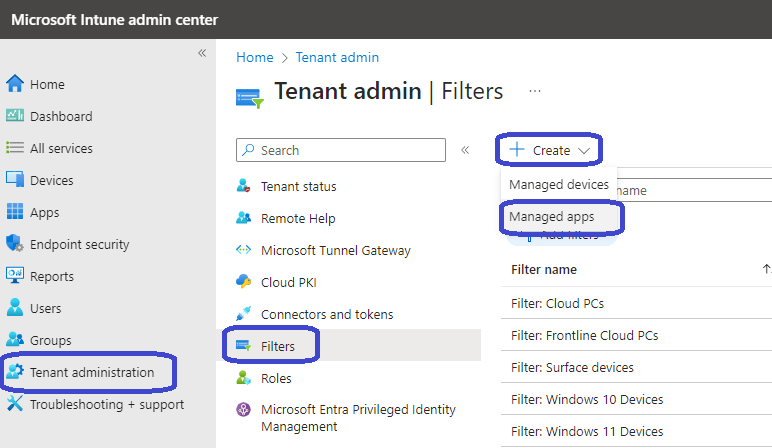
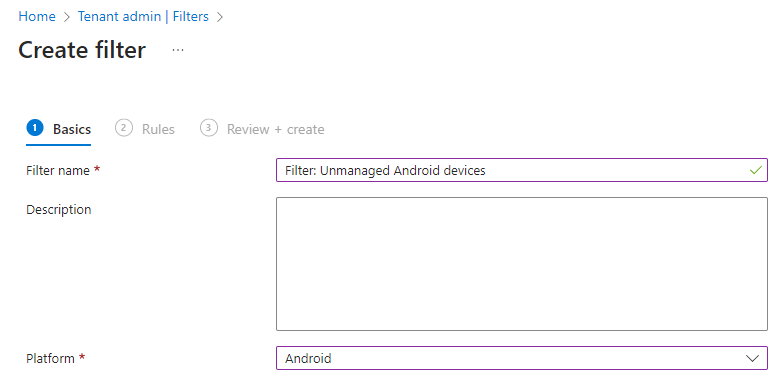
Create an Intune device filter
From the Microsoft Intune admin center, go to Tenant admin, Filters. Click the + Create button in the ribbon and select Managed Apps.
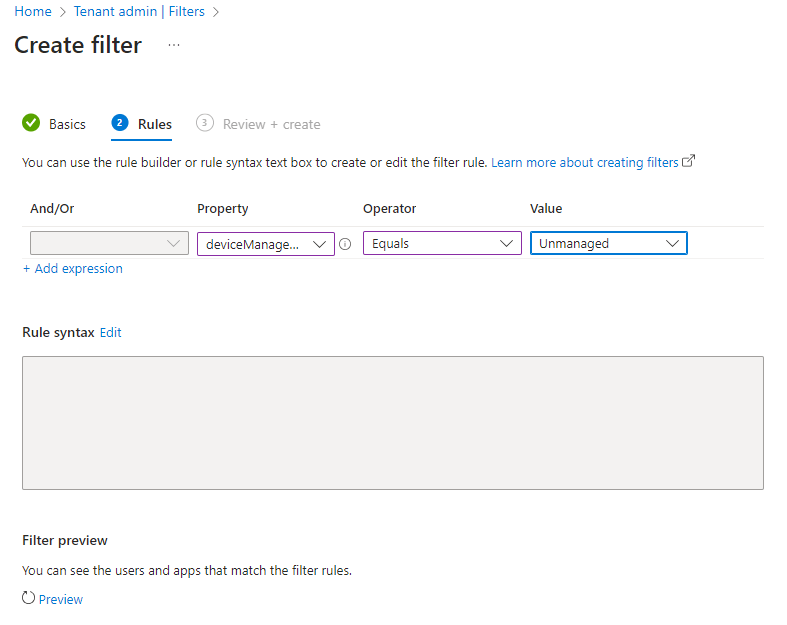
Provide a name and a description and continue to the Rules tab.
Select the following expression:
- Property: deviceManagementType
- Operator: Equals
- Value: Unmanaged
You’ll end up with the following: (app.deviceManagementType -eq “Unmanaged”)
Take a moment to admire your awesome work and create the filter.
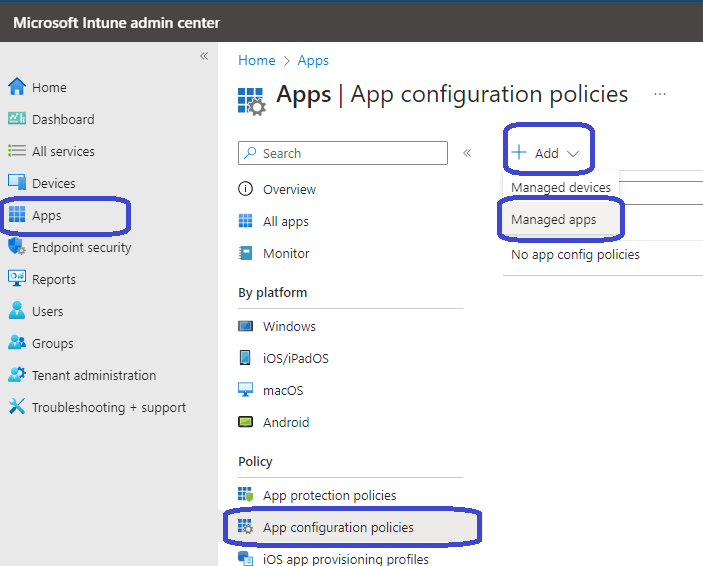
Create an Intune app configuration policy
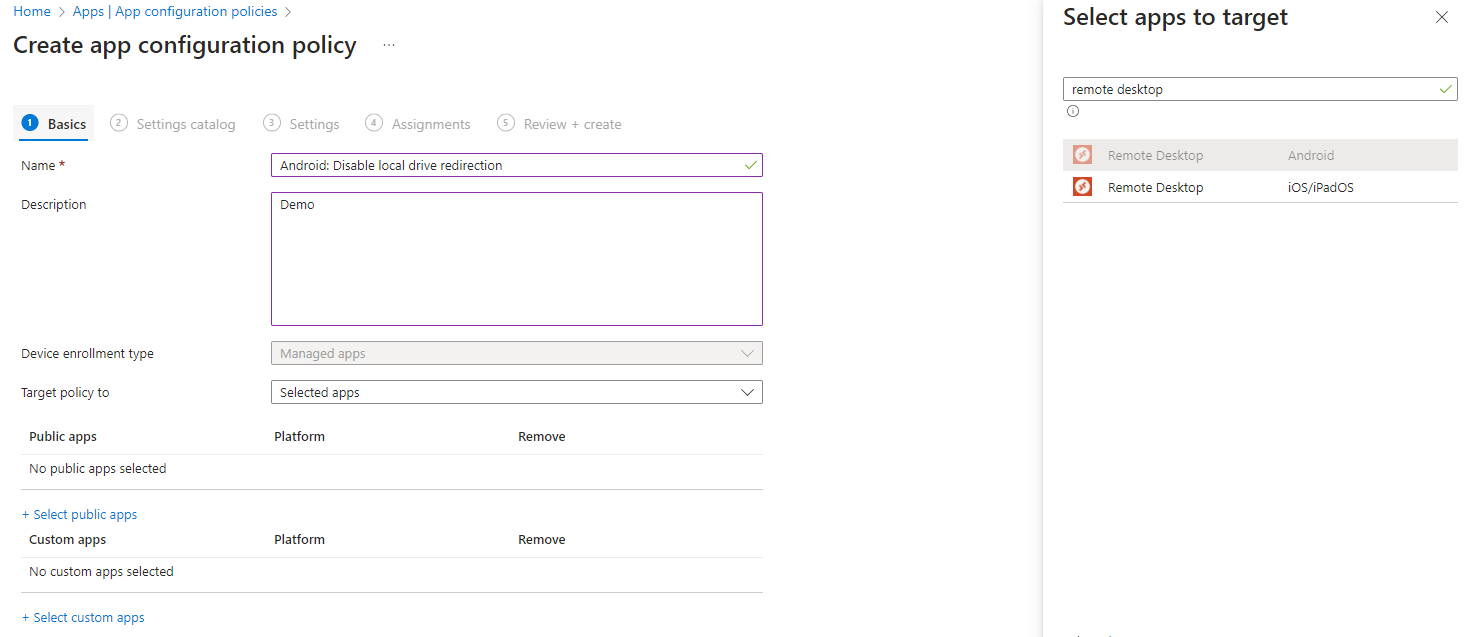
From the Microsoft Intune admin center, go to Apps, App configuration policies, select + Add in the ribbon and select Managed apps.
Configure the following items:
- Give the policy a name and a description.
- Target the policy to: Selected apps.
- Click on select public apps and add Remote Desktop Android.
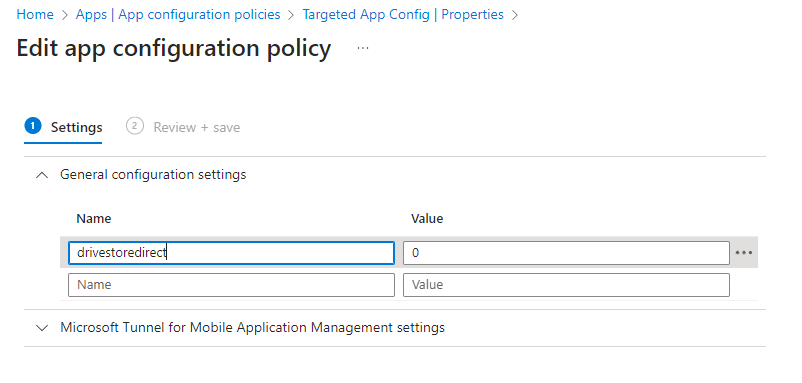
We can ignore the second tab (settings catalog) in the app configuration policy. Continue to the third tab called Settings. Add the desired setting in the General configuration settings overview. I will add drivestoredirect since I want to demo local drive redirection. Other valid settings are listed here (link).
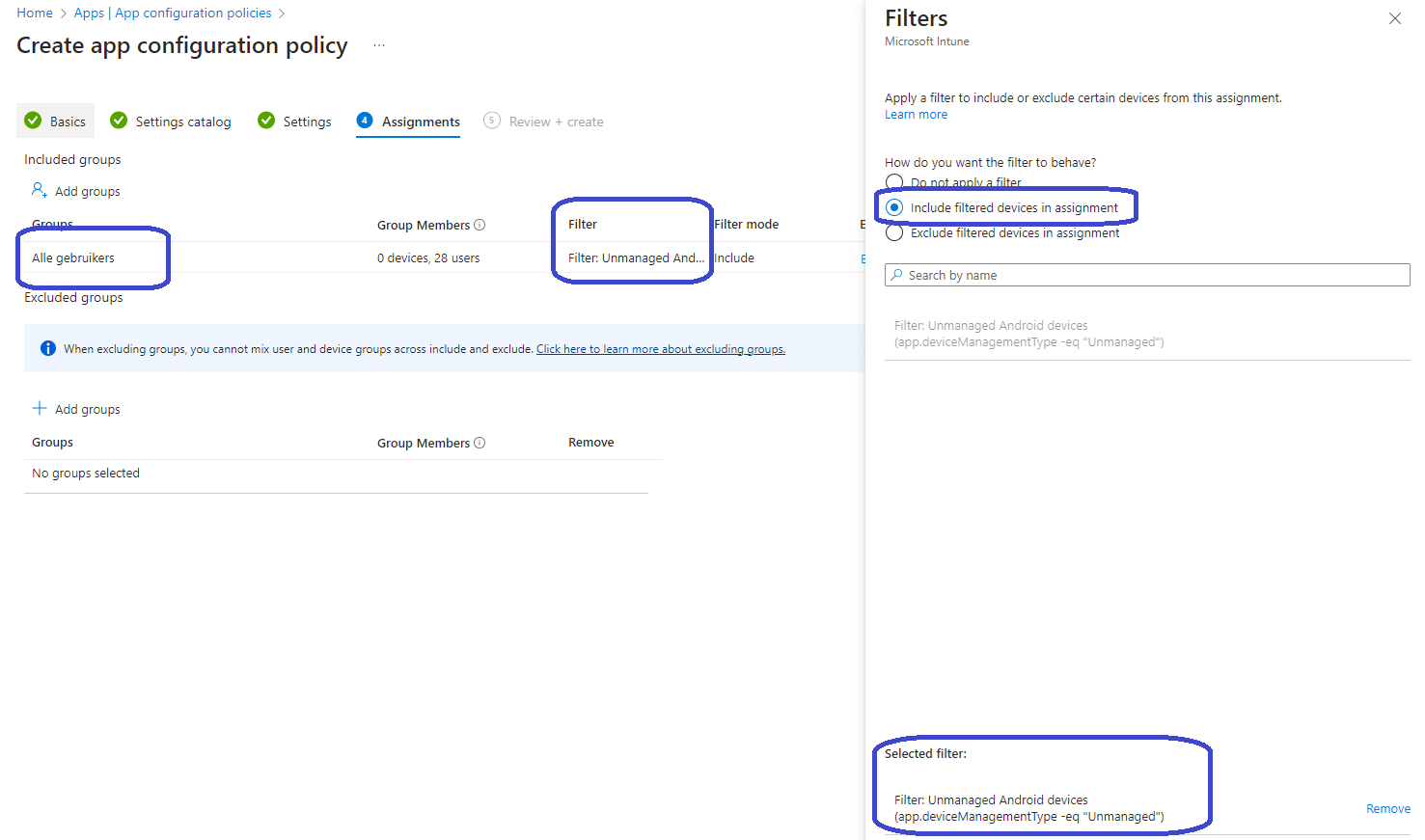
Now it’s time to assign the app configuration policy. The way to do so is by assigning the policy to All users or a group of users and use the previously created App Filter.
Finish up and create the policy. I ended up with the following:
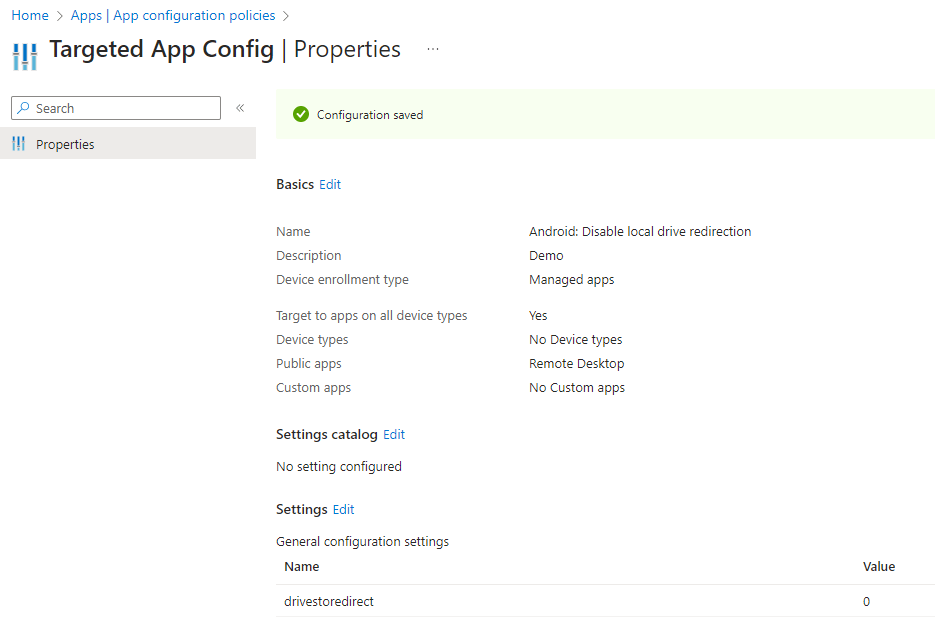
All that is left to do is to wait until the 720 minutes have past and the local drive redirection will be disabled for unmanaged Android devices.
Resources
Share this:
- Click to share on LinkedIn (Opens in new window) LinkedIn
- Click to share on X (Opens in new window) X
- Click to share on Facebook (Opens in new window) Facebook
- Click to share on WhatsApp (Opens in new window) WhatsApp
- Click to share on Telegram (Opens in new window) Telegram
- Click to print (Opens in new window) Print











One Comment
Comments are closed.