What’s up, everyone!
Here is a real world example where users got the message ‘Get access to this resource’ when the Microsoft Teams desktop app starts. The message also tells us a bit more ‘This device does not meet your organization’s compliance requirements’.
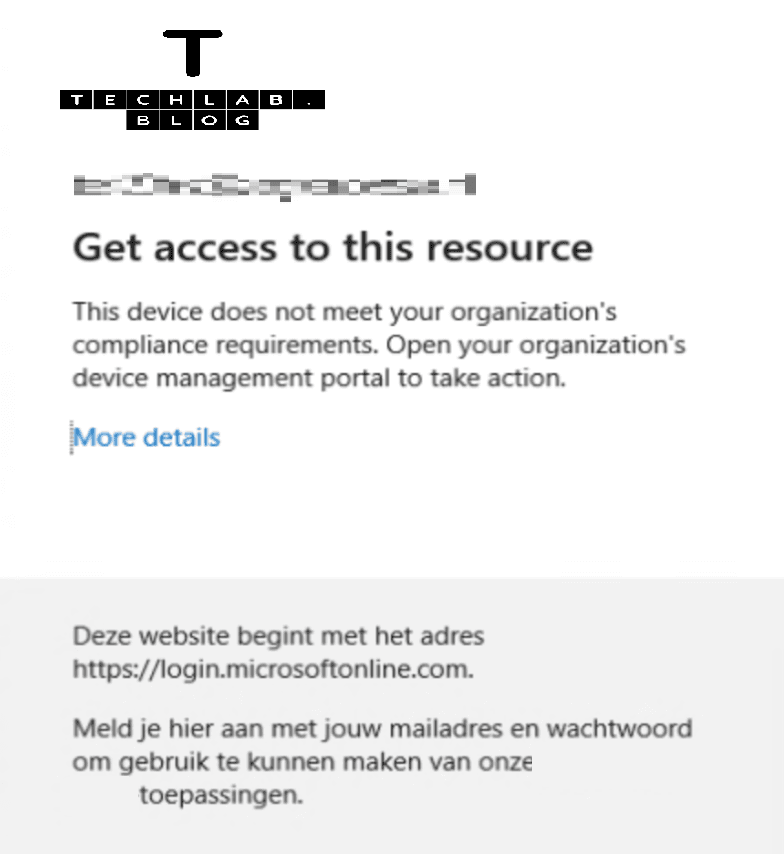
There could be many reasons why this message appears. In this troubleshooting guide I will explain the basic steps we can take to solve this issue.
Where to look
The following portals will help us to troubleshoot;
It’s best to log in both portals and set them side-by-side in your screen.
Troubleshooting
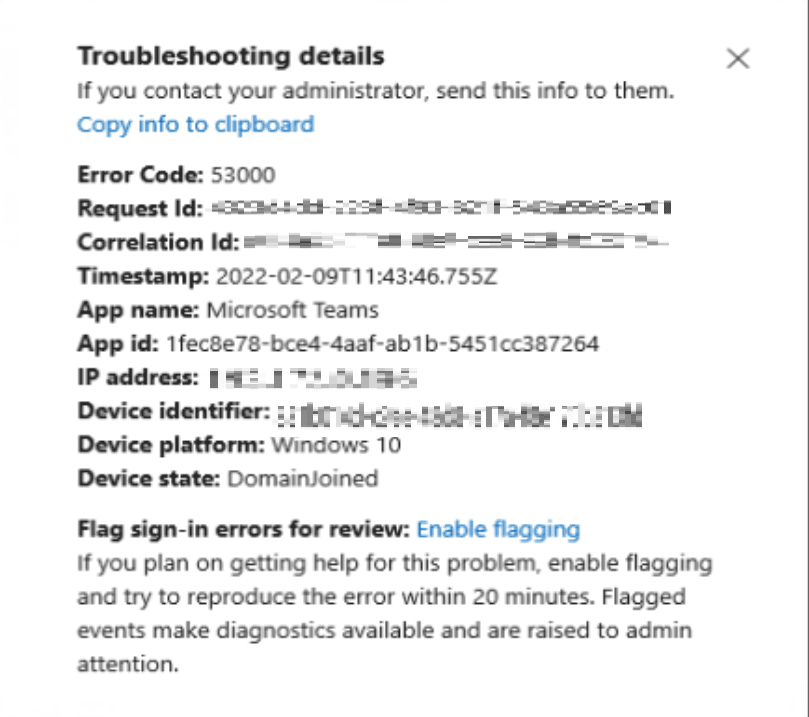
At this point all we know is that a conditional access policy blocks us from accessing the Microsoft Teams desktop app. Users who receive this message have to option to click on a More details option.
This will show us some technical information. However, if the user didn’t send us a screenshot of this information we can make do with the username and the date and timestamp.
If we do have the Correlation Id, we can just search on that to find the login attempt.
In the Azure portal, open up the Azure Active Directory blade and click on Sign-In logs from the Monitoring group.
This page will provide us with an overview of the sign-ins.
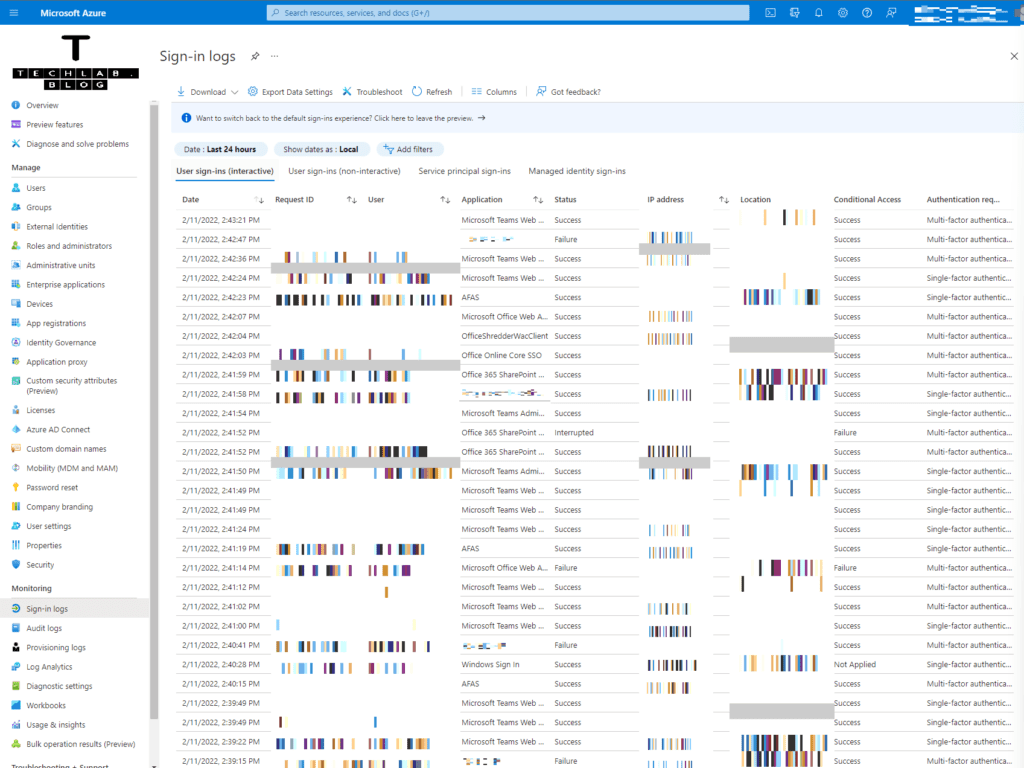
We can set filters on top of the screen. There are many attributes we can use to filter the sign-in events.
For example, we can filter on the request id and/or the correlation id which the users sees after clicking on More details. We can filter on the failure status or the username. Choose which attribute suits you the best.
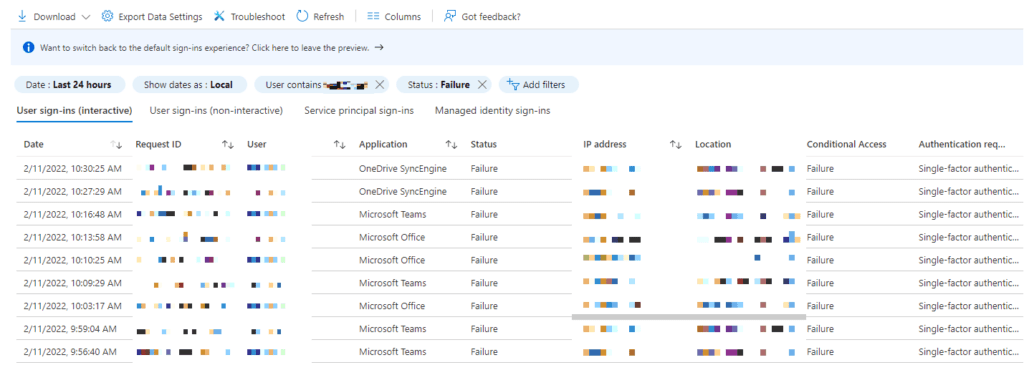
This view is filtered on user and status ‘Failure’.
We can click on the related sign-in event. On the right-side a new blade will appear with the relevant information. There are a couple of tabs at the time of writing;
- Basic info: Gives us generic information regarding the sign-in event.
- Location: Tells us the IP address and the estemated city where the sign-in originated from. It also shows if the IP address matches a Named Location or Trusted Location.
- Device info: Shows generic information about the Device ID, browser, operating system, if the system is compliant, managed and the join type.
- Authentication details: Provides information on the authentication status.
- Conditional Access: This tab shows all of the Conditional Access policies and if they were applied during this sign-in event. It also shows detailed information per policy.
- Report-only: Shows conditional access policies which are set to Report-Only.
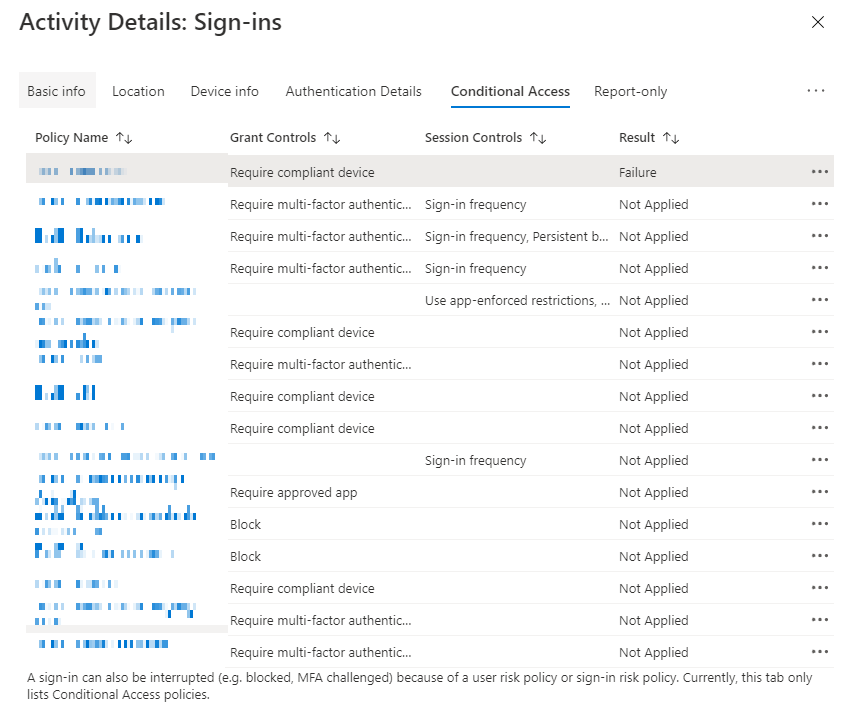
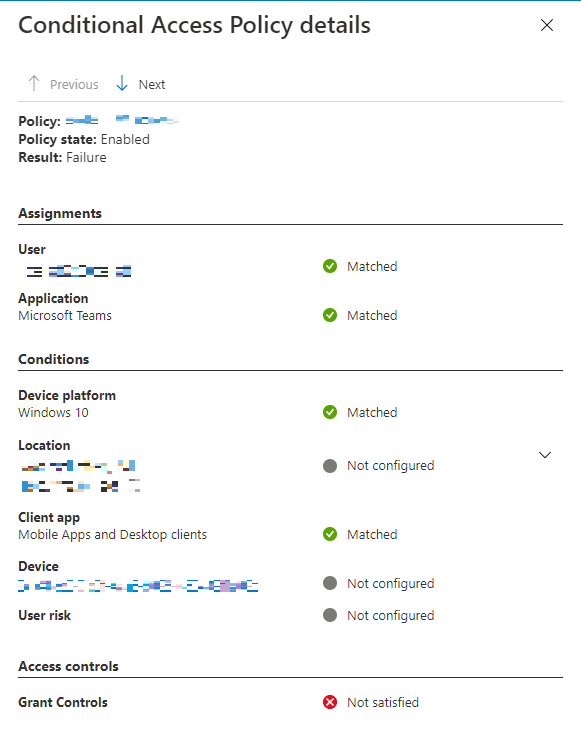
This real-world example shows the sign-in has failed because the device was not compliant.
Now that we know why the sign-in event failed, we can work towards a solution.
In my case, the device compliance was not needed. So the solution was to exclude the hosts via a location in the conditional access policy in the Endpoint Manager console.
It’s worth noting that sign-in events can be viewed in the Endpoint Manager portal. Open the users blade and click on the Sign-In logs under the Activity group. This blade opens the same blade from Azure AD.
Share this:
- Click to share on LinkedIn (Opens in new window) LinkedIn
- Click to share on X (Opens in new window) X
- Click to share on Facebook (Opens in new window) Facebook
- Click to share on WhatsApp (Opens in new window) WhatsApp
- Click to share on Telegram (Opens in new window) Telegram
- Click to print (Opens in new window) Print